In today’s fast-paced digital landscape, 5G unified communications (UC) are revolutionizing the way we connect, collaborate, and conduct business. However, with great potential comes great responsibility, as organizations must navigate the complexities of addressing security concerns in this cutting-edge technology. In this comprehensive guide, we’ll delve into the essential best practices and solutions for ensuring a secure 5G UC ecosystem, empowering you to harness the transformative power of 5G without compromising on data protection and privacy. Stay ahead of potential threats and confidently embrace the future of communication by exploring our expert insights on safeguarding your 5G UC infrastructure.
Assess risks in 5G infrastructure
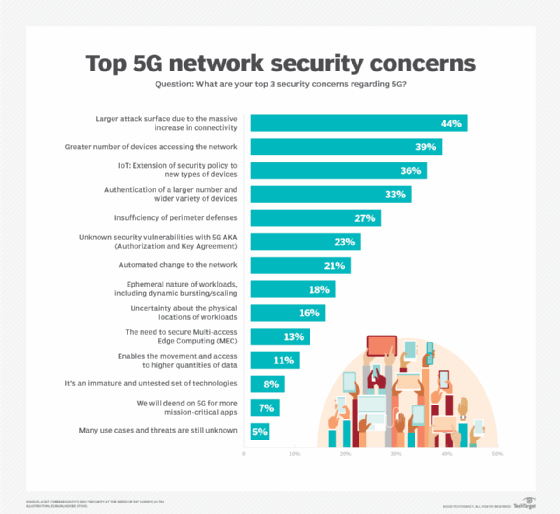
In addressing security concerns for 5G UC, comprehensively assessing risks in the 5G infrastructure is crucial. Effectively identifying vulnerabilities, threats, and potential attack vectors allows for proactive solutions and enhanced network integrity. Implementing robust risk management practices ensures seamless connectivity and safeguards sensitive data, keeping users confidently connected in the evolving digital landscape.
Implement robust network security measures

Embrace top-notch network security measures to keep 5G UC on lock! Safeguard your system by deploying firewalls, encryption, and intrusion prevention systems (IPS). Stay vigilant by regularly updating software, monitoring traffic patterns, and identifying potential threats. Don’t just protect, but flex your cyber muscles to ace the security game!
Regularly update and patch systems

Stay ahead in the 5G game by consistently updating and patching your systems. Regular maintenance keeps security threats at bay and ensures smooth functioning of your Unified Communications (UC) infrastructure. Embrace a proactive approach and safeguard your network from potential vulnerabilities, providing top-notch security for your 5G UC ecosystem.
Employ end-to-end encryption methods

Embrace end-to-end encryption techniques to ensure top-notch security in 5G UC. By employing powerful encryption algorithms, you can protect sensitive data from prying eyes and cybercriminals. Stay ahead of the game and safeguard your network, devices, and communication channels with robust encryption methods. Peace of mind? It’s encrypted!
Monitor for potential threats continuously
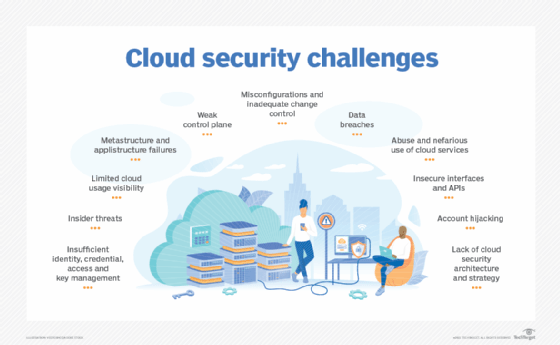
Always stay vigilant in the 5G UC landscape by consistently monitoring for potential threats. Implement cutting-edge security tools, like AI-driven threat detection systems, to proactively identify and mitigate risks. This continuous monitoring approach keeps your network secure and ensures a seamless user experience, safeguarding your data and reputation.
Train staff on 5G security protocols

Empower your team by providing comprehensive training on 5G security protocols. This crucial step ensures that staff members are well-versed in recognizing potential threats and implementing the latest security measures to safeguard your 5G UC infrastructure. Investing in employee education is vital for minimizing risks and maintaining a secure network.


GIPHY App Key not set. Please check settings