AWS Security Groups are a great way to protect your cloud-based resources, but do you know if they’re stateful? In this article, we’ll explore what stateful security groups are and how you can use them to further secure your resources in the Amazon Web Services (AWS) environment. We’ll discuss the benefits and drawbacks of using stateful security groups, as well as provide tips and best practices for setting up and managing them. Read on to learn more about AWS Security Groups and how you can use them to keep your cloud resources secure.
What is Stateful Firewalling in AWS Security Groups?
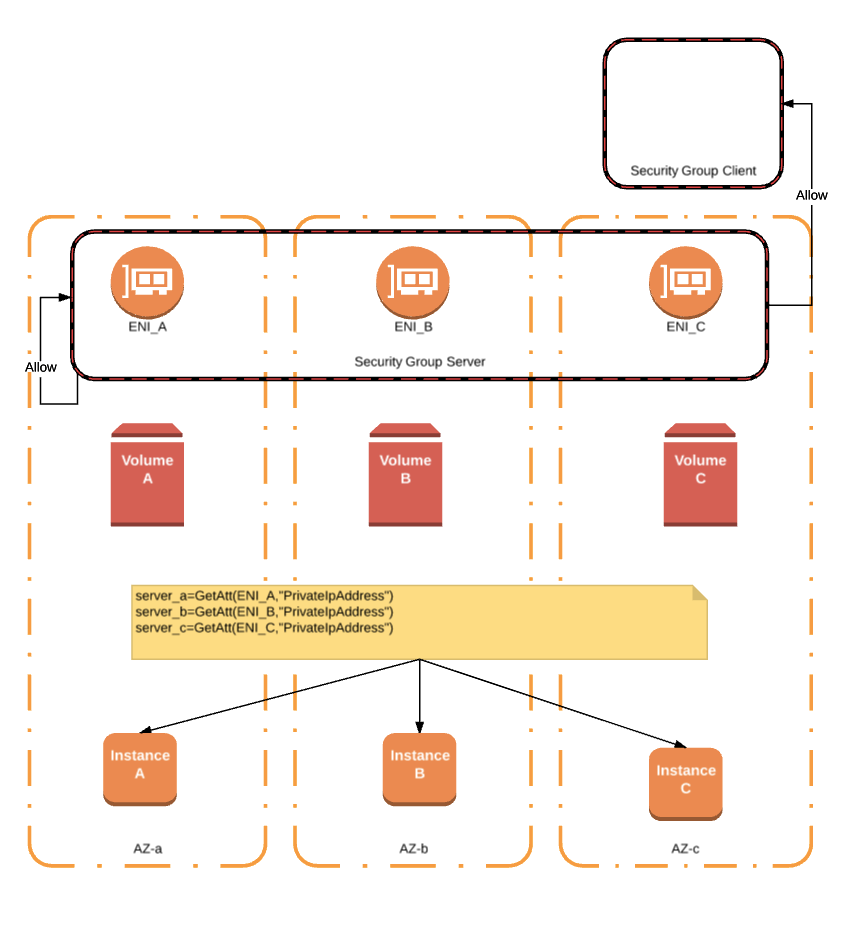
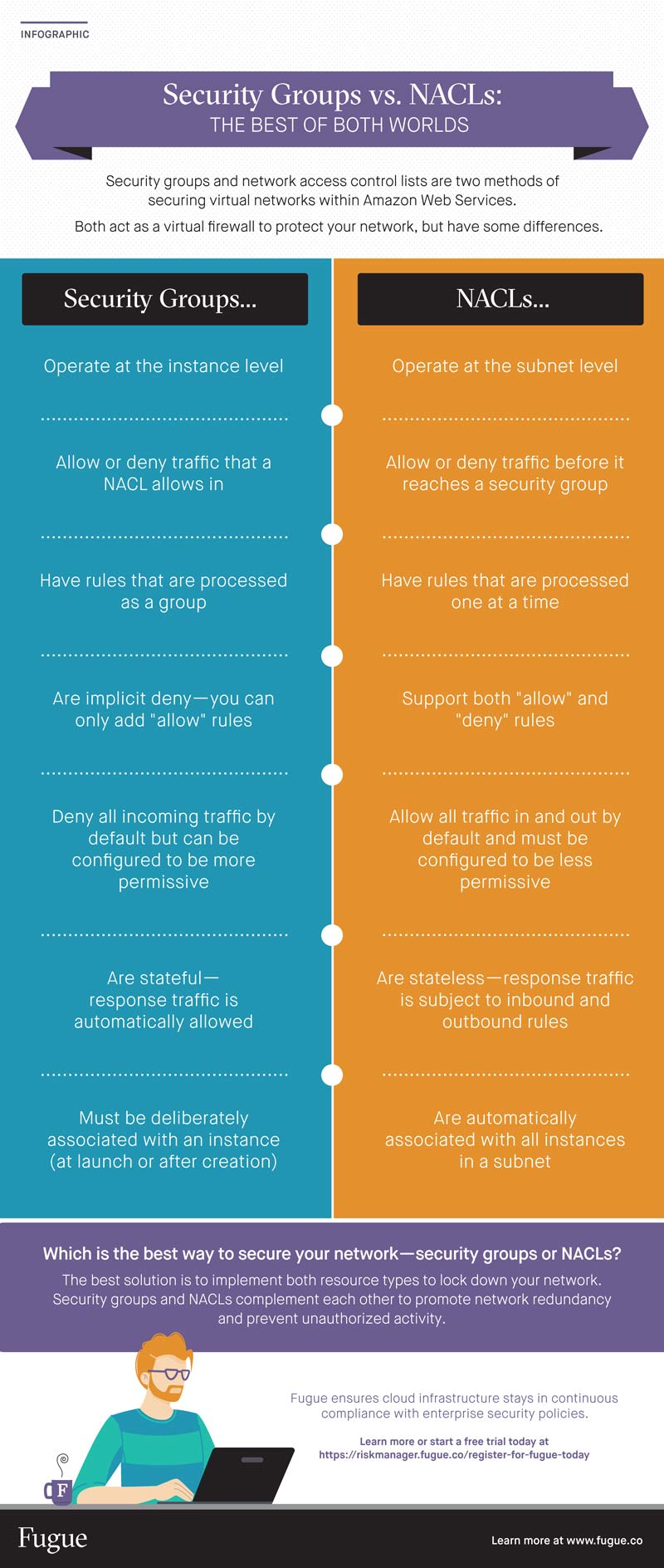
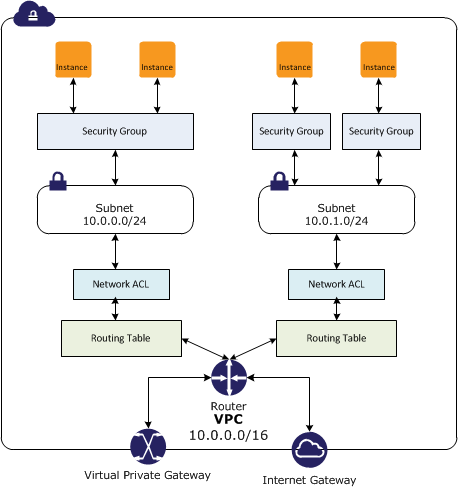
A stateful firewall in AWS Security Groups is an amazing way to keep your AWS environment safe and secure. It provides an extra layer of security by monitoring incoming and outgoing traffic and only allowing the traffic you specify. This way, any malicious traffic is blocked before it can even reach your resources. You can set up specific rules to only allow certain types of traffic or block certain ports or IP addresses to further protect your AWS environment. With stateful firewalling, you can rest assured that your data and resources are secure. It’s an essential part of any AWS security strategy and is an easy way to protect your cloud environment.
The Benefits of Utilizing Stateful Firewalling in AWS Security Groups
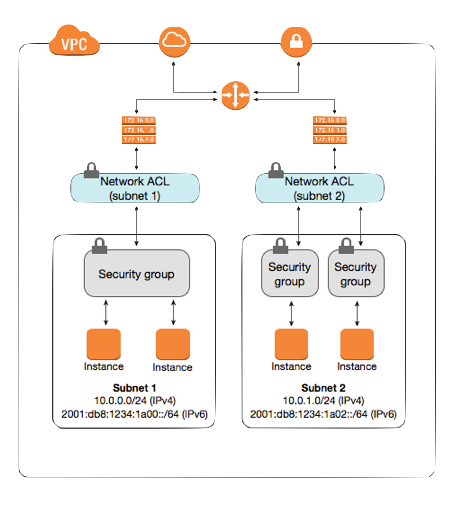
Using stateful firewalling in AWS Security Groups is a great way to keep your cloud environment secure. Not only does it help protect your data from malicious attacks, but it also helps to ensure that only the appropriate traffic is allowed access to your cloud environment. It also provides a more granular level of control over the traffic that is allowed into and out of your cloud environment. This allows you to easily monitor and control the traffic that is allowed in and out of your cloud environment, making it easier to detect and prevent malicious activity. Stateful firewalling also allows you to easily create rules that can be applied to your entire cloud environment, making it easier to manage and secure your cloud environment. By utilizing stateful firewalling in AWS Security Groups, you can make sure that your cloud environment is secure and that only the right traffic is allowed in or out.
Commonly Used Security Rules in AWS Security Groups
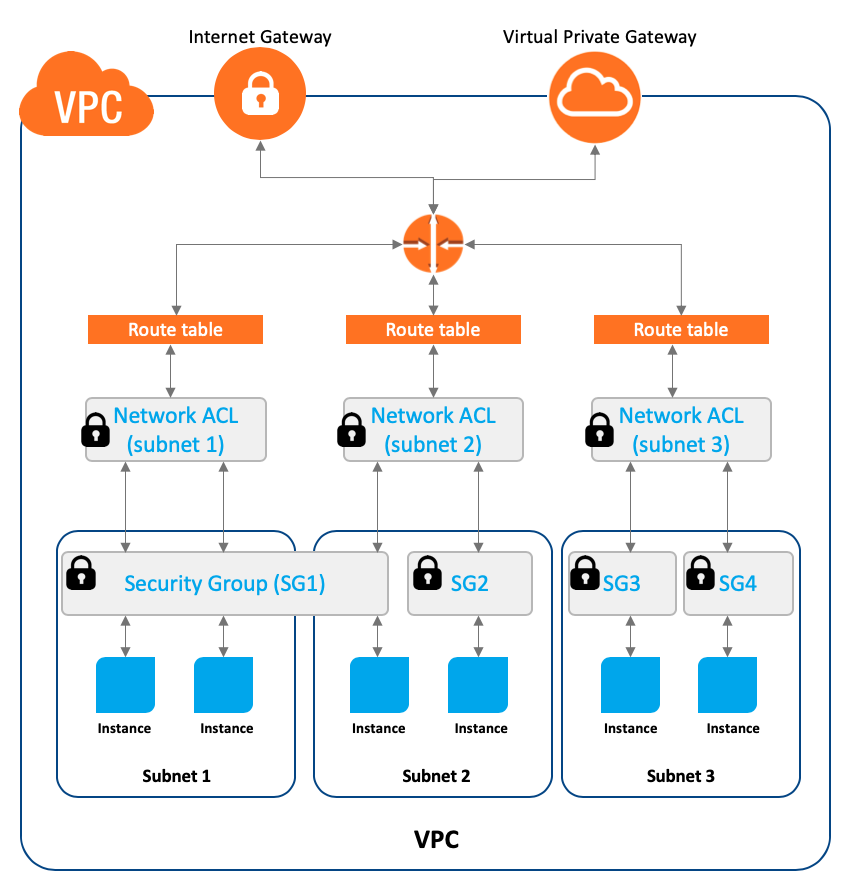
AWS Security Groups are one of the most commonly used security rules when it comes to protecting your resources on the cloud. Not only do they provide you with an extra layer of protection, but they are also stateful, meaning that any incoming or outgoing traffic is tracked and monitored. This allows you to create rules that allow or deny specific traffic based on IP, port, and protocol, giving you full control over who can access your resources. AWS Security Groups are an essential part of keeping your data and applications secure, so it’s important to make sure you’re taking advantage of them when you’re using the cloud.
Best Practices for Configuring AWS Security Groups
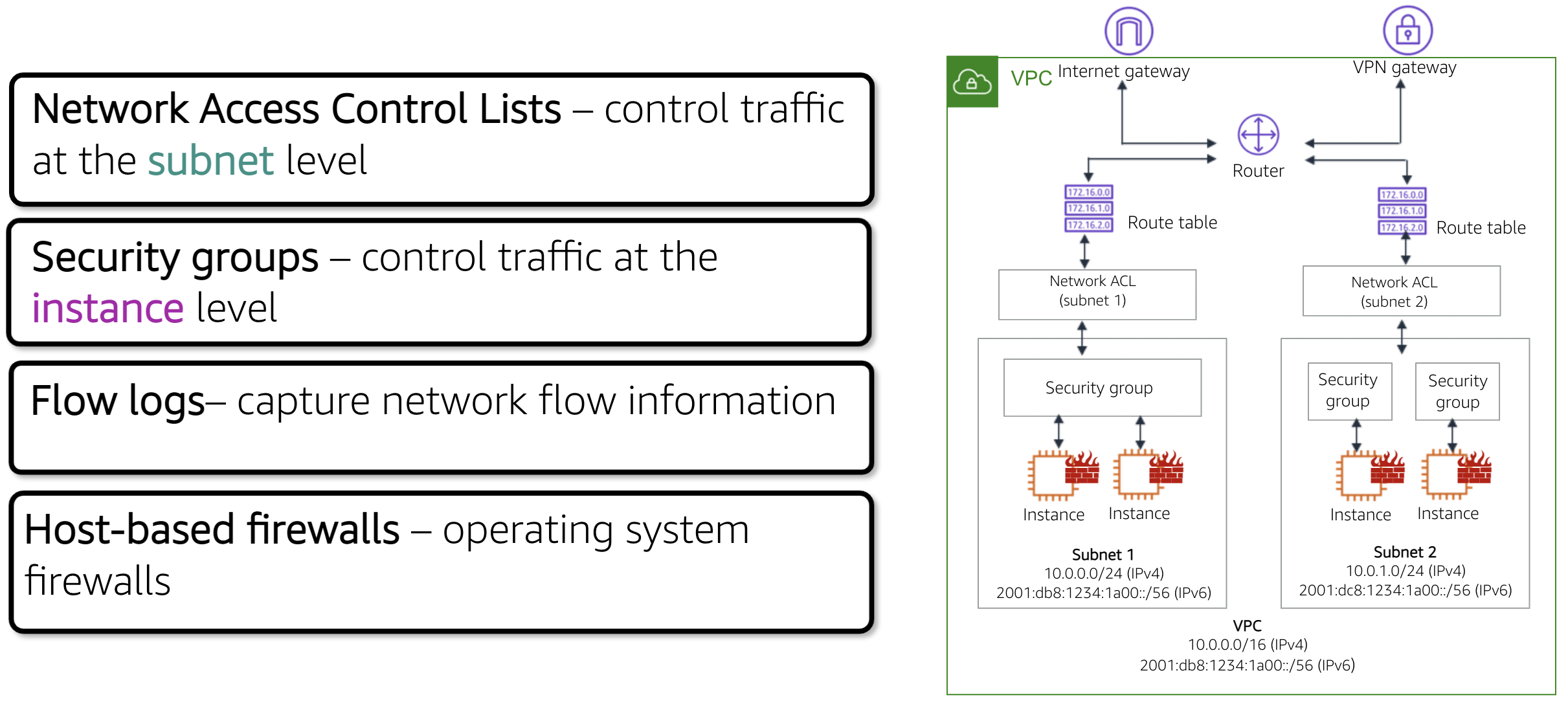
If you’re using AWS Security Groups, it’s important to follow best practices in order to keep your environment secure. One of the best practices is to limit access to the ports and protocols needed for your application or service. This will help prevent unwanted traffic from entering your network and potentially malicious actors from gaining access. Additionally, it’s important to keep your security groups up-to-date and regularly check for any changes or new rules that need to be added. Finally, be sure to limit access to specific IP addresses or ranges, rather than allowing access from any IP address. By following these best practices, you can be sure that your AWS Security Groups are keeping your environment safe and secure.
How to Monitor and Troubleshoot AWS Security Groups to Ensure Maximum Security
.Monitoring and troubleshooting AWS security groups is essential to ensure maximum security. To do this, start by configuring alerts for any unauthorized changes to your security groups. This way, you can be alerted when someone attempts to make changes, and you can take steps to prevent them from doing so. Additionally, check the rules of your security group periodically to make sure they are up-to-date and accurate. If you find any rules that are no longer necessary, you can delete them, and if you need to add new rules, you can do so as well. Finally, use Amazon CloudWatch to monitor your security groups and any associated traffic. This can help you identify any suspicious activity, and you can then take steps to protect your resources. By following these steps, you can stay on top of your security groups and ensure maximum security.


GIPHY App Key not set. Please check settings