As an 18-year-old student, have you ever been curious about how to hack a computer? If yes, then you’ve come to the right place! This article will provide you with the necessary information and steps to help you understand the basics of computer hacking. We’ll cover the tools and techniques used by hackers, the ethical considerations to keep in mind, and the best practices to avoid getting caught. So, get ready to explore the exciting world of computer hacking!
Research computer security weaknesses.
As a student, it’s important to research computer security weaknesses when trying to hack a computer. Understanding the inherent vulnerabilities of a system is the first step to exploiting them. This can be done by researching and reading up on the latest security news and known vulnerabilities, or even by studying the source code of target systems. This way, you can find the weaknesses that allow you to get access to a computer and then exploit them.
Acquire hacking tools and knowledge.

If you want to learn how to hack a computer, you’ll need to get the right tools and knowledge. There are plenty of tutorials and guides available online, but it’s important to choose the right ones. Popular hacking tools like Kali Linux and Metasploit are a great start, and you can also take courses or read books to learn the basics. With a bit of practice and dedication, you can become an expert hacker in no time.
Create malicious code.

Creating malicious code is an essential part of hacking a computer. It involves writing a program or script that can be used to access a computer system without the user’s permission. It can be done using a variety of programming languages, but it is important to make sure the code is well written and secure so that it won’t be detected. Additionally, it is important to keep up to date with the latest hacking techniques and tools in order to stay ahead of the game.
Exploit computer vulnerabilities.
Exploiting computer vulnerabilities is a key part of hacking a computer. It’s a way of finding weaknesses in software and hardware in order to gain access to a system. This can be done by using various attack methods such as buffer overflows or by using exploit kits. It’s important to be up to date with the latest vulnerabilities in order to be successful in this type of attack.
Install malicious payloads.

Installing malicious payloads is an important part of hacking a computer. It’s a way for hackers to gain access to a system and carry out a variety of tasks. This can be done by introducing malicious code into the system, or by disguising a legitimate program as a malicious one. It’s important to note that this is a dangerous step and should only be done by experienced hackers. Be sure to have all the necessary protection in place before attempting to install malicious payloads.
Monitor access and activity.
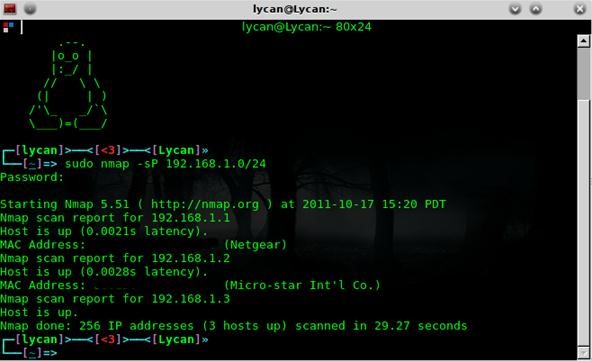
Monitoring access and activity on your computer is key when it comes to hacking. It’s important to keep track of who is connecting to your computer and what they’re doing on it. You can use programs like Wireshark to monitor network traffic and detect suspicious activity. You can also use security tools like OSSEC to detect and alert you to any malicious activity. It’s important to stay vigilant and keep an eye on your computer’s access and activity.




GIPHY App Key not set. Please check settings