AWS Shield is a powerful security solution designed to protect your applications and services from malicious cyberattacks. It provides advanced capabilities to help protect against distributed denial of service (DDoS) attacks and provides real-time protection from a wide range of threats. This article will explain how AWS Shield works and how it can be used to help protect your applications and services from malicious activity. Get ready to learn about the powerful defense system that will help keep your business secure!
Overview of AWS Shield and its Uses
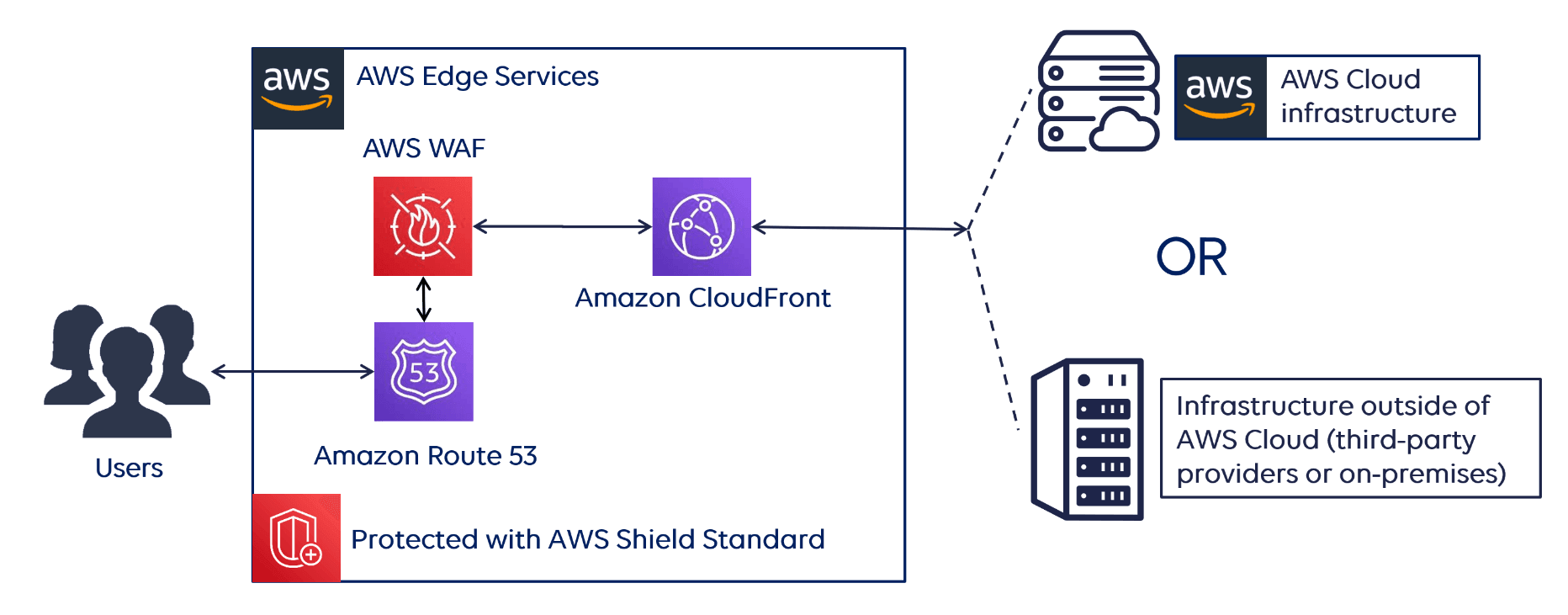
AWS Shield is an amazing tool that helps protect your cloud services from malicious cyber attacks and other threats. It provides advanced protection against Distributed Denial of Service (DDoS) attacks, as well as detecting and blocking malicious traffic. It also provides continuous monitoring of potential threats, and the ability to quickly respond to incidents. With AWS Shield, you can protect your applications from malicious actors and keep your cloud services running smoothly. AWS Shield gives you the peace of mind knowing that your cloud services are protected from the latest threats. It is a great tool to have in your security arsenal and can help you keep your cloud environment safe from malicious attackers.
How AWS Shield Protects Your Website from Attacks
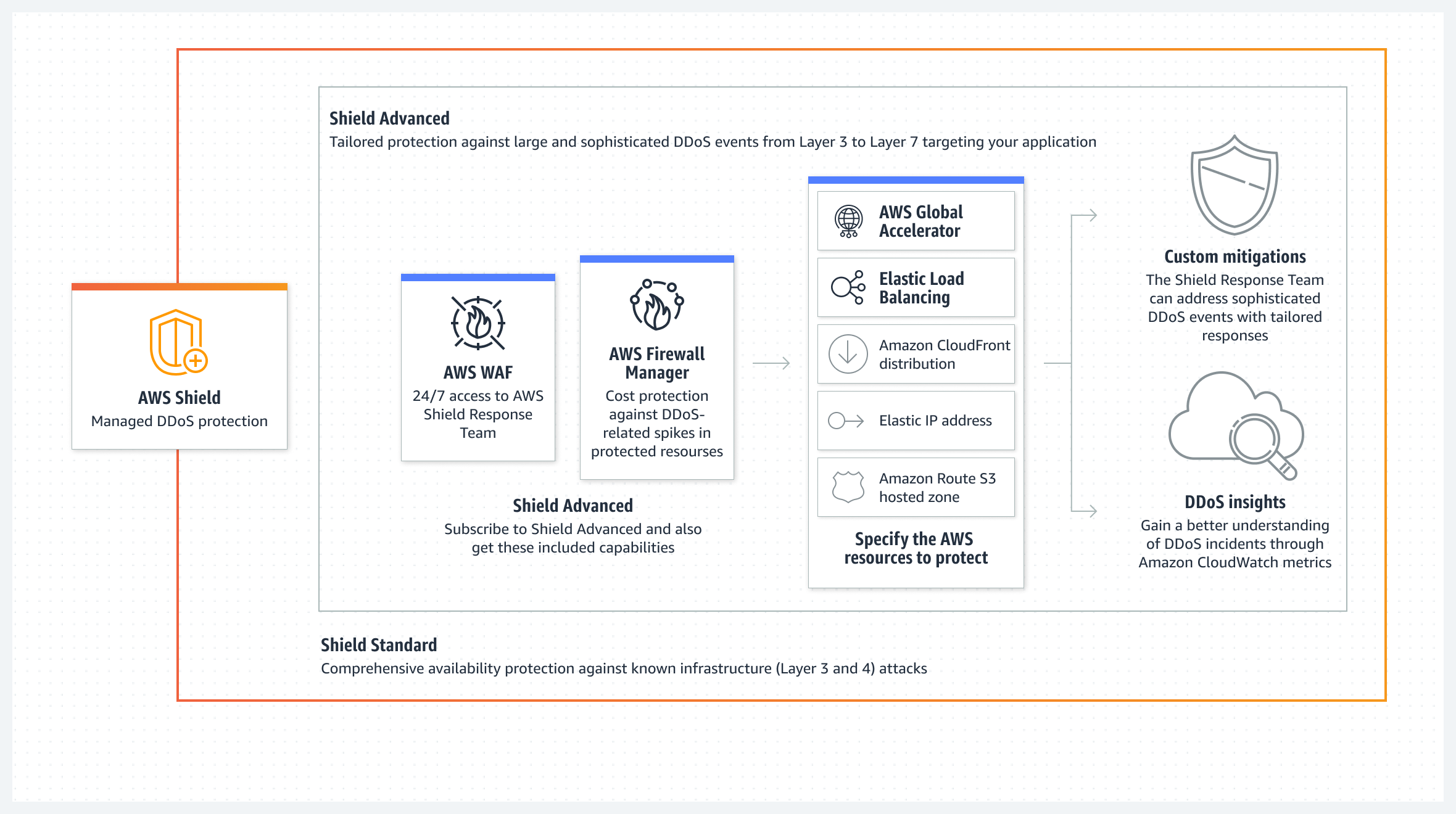
AWS Shield is a great way to protect your website from malicious attacks. It helps keep your website safe from DDoS attacks and provides extra layers of protection for any web application you have running. The Shield also monitors traffic and provides real-time feedback on any suspicious activity. It’s an easy way to keep your site secure, and the best part is it’s totally free. It’s an essential tool for any website that wants to stay secure and protected from malicious attacks. With AWS Shield, you can ensure your website is safe and secure, and you can rest easy knowing your site is protected against any would-be attackers.
The Different AWS Shield Security Features
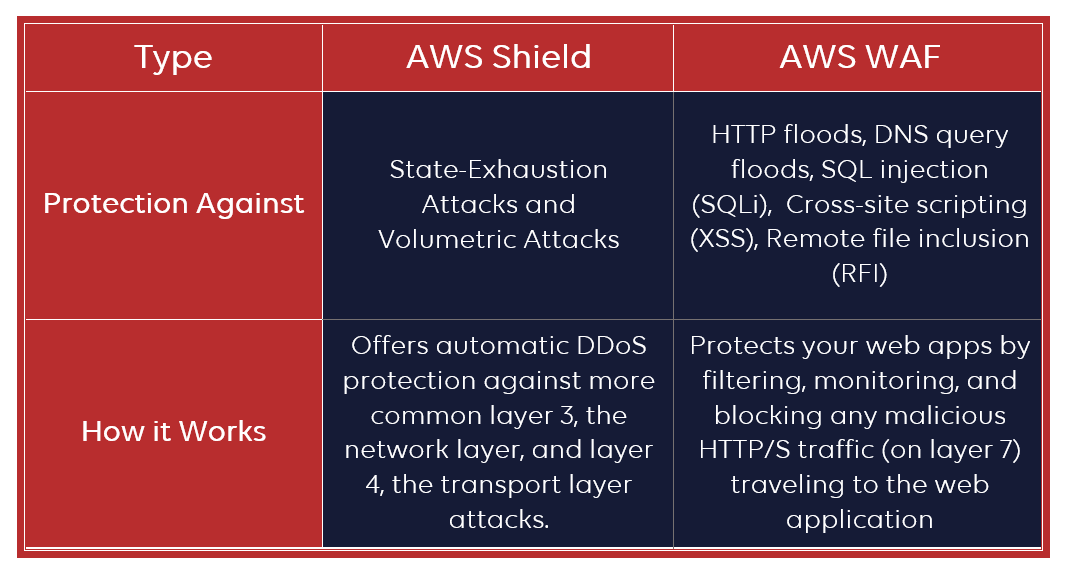
AWS Shield provides an array of security features that keep your data and applications safe from malicious attacks. These features include automated threat detection, IP reputation management, and protection against DDoS attacks. Automated threat detection uses a combination of machine learning and signature-based detection to identify and block malicious traffic before it reaches your applications. IP reputation management helps to ensure that IP addresses associated with malicious activity are blocked. Finally, AWS Shield provides protection against distributed denial-of-service (DDoS) attacks. This feature helps ensure that your applications remain available even if they are subjected to a large amount of malicious traffic. With these security features, you can rest assured that your data and applications are secure and protected from malicious actors.
How to Set Up AWS Shield and Implement It Properly
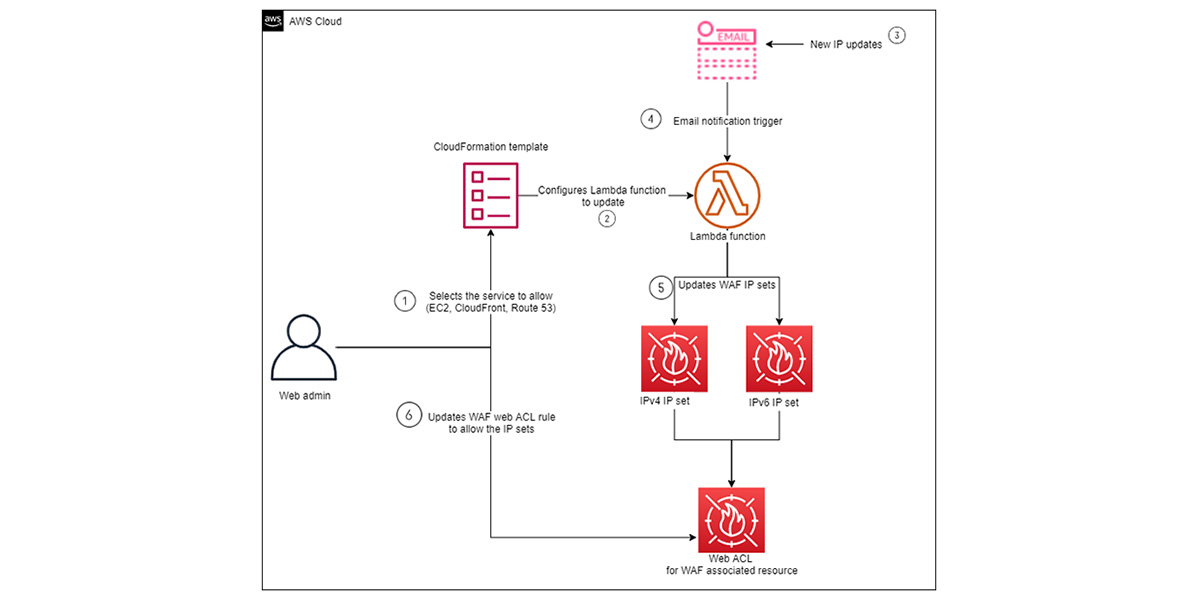
Setting up AWS Shield is essential to keep your web application secure and protect it from malicious attacks. To get started, you’ll need to sign up for an AWS account and create an Amazon Virtual Private Cloud (VPC). Once you have your VPC set up, you will be able to configure AWS Shield to protect your web application. You’ll need to create an access control list (ACL) and an AWS WAF rule. The ACL will specify which traffic is allowed to enter your VPC and the WAF rule will filter out malicious traffic. Once you have these two elements set up, you can turn on AWS Shield and start protecting your web application from attackers. With AWS Shield, you can also monitor your web application for suspicious activity and block malicious requests. With the proper implementation of AWS Shield, your web application will be safe from malicious attacks and you can rest easy knowing your data is secure.
Best Practices for Using AWS Shield to Protect Your Website
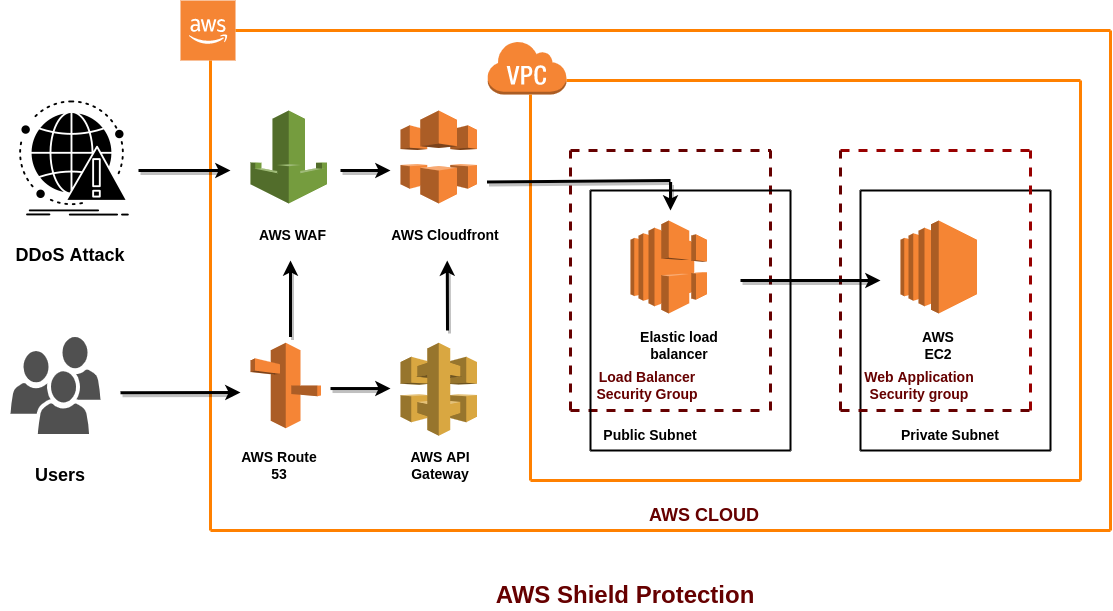
If you’re looking to protect your website from malicious attacks, using AWS Shield is a great way to do it. With this service, you can guard your site against DDoS attacks, as well as other malicious activities. To ensure you get the most out of your AWS Shield protection, there are a few best practices you should follow. First, make sure your website is properly configured for AWS Shield. This means having the right security protocols in place and up-to-date software. Secondly, keep an eye on your website performance metrics and be sure to monitor for any sudden spikes in traffic or other odd behavior. Lastly, use AWS Shield’s additional services, such as Web Application Firewall and Advanced, to further secure your website. By following these best practices, you can rest assured that your website is secure and protected from attacks.



GIPHY App Key not set. Please check settings