As we enter the exciting era of lightning-fast 5G networks, businesses worldwide are eagerly embracing the benefits of enhanced Unified Communications (UC) capabilities. However, with great power comes great responsibility, and addressing security concerns in 5G UC is paramount to protect sensitive data and prevent cyber threats. In this comprehensive guide, we’ll explore best practices and innovative solutions to fortify your organization’s defenses, safeguarding your vital assets and ensuring seamless connectivity in the age of hyper-connectivity. Stay ahead of the curve and confidently ride the 5G wave with our expert advice and insights.
Assess risks in 5G infrastructure
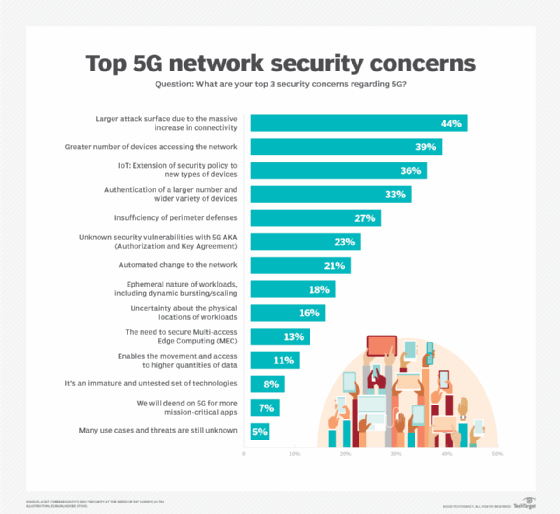
In order to tackle security concerns in 5G Unified Communications (UC), it’s crucial to first assess the risks associated with the 5G infrastructure. By identifying potential vulnerabilities, organizations can effectively implement robust security measures, ensuring seamless connectivity and data protection. Thorough risk assessments help in addressing challenges and adopting best practices for a secure 5G UC experience.
Implement robust encryption and authentication

Embrace top-notch encryption and authentication techniques to safeguard your 5G UC experience. By implementing robust security measures, you can effectively combat cyber threats and protect sensitive data. Adopting advanced encryption algorithms and reliable user authentication methods ensures a secure and seamless communication network, keeping potential hackers at bay. Stay connected and secure with confidence!
Monitor network traffic for anomalies

Keep a keen eye on your 5G UC network traffic to swiftly spot any anomalies that might signal security threats. Implementing advanced monitoring tools and network analytics empowers you to detect and tackle potential issues before they escalate. Stay proactive and safeguard your ultra-connected world with robust security measures.
Adopt Zero Trust security approach

Embrace the Zero Trust security approach to tackle 5G UC security concerns effectively. This strategy assumes no inherent trust within networks and requires continuous verification for all users and devices. Implementing Zero Trust principles enhances your security posture, protecting sensitive data from unauthorized access and potential cyber threats.
Regularly update software and protocols

Stay ahead of cyber threats by consistently updating your software and protocols in 5G UC networks. Timely upgrades help close security loopholes, ensuring top-notch protection for your data. So, don’t slack on this crucial step and maintain a robust defense against hackers by always keeping your network up-to-date.
Train staff in cybersecurity practices
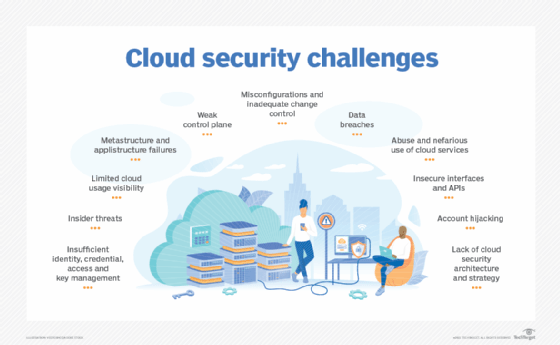
Empowering your workforce with robust cybersecurity knowledge is crucial in fortifying 5G UC defenses. Invest in comprehensive training programs that educate employees on potential threats, safe online behavior, and incident response protocols. A well-informed team can act as the first line of defense, mitigating risks and enhancing overall security in the 5G landscape.

GIPHY App Key not set. Please check settings